Packets Sniff Sniff
13 Oct 2020 - Jake Sherwood
 Packets Sniff Sniff
Packets Sniff Sniff
Packets Sniff Sniff
Diving deeper into network analysis, this week we explored packet sniffing with Wireshark.
A few things I tried:
Wireshark Exploration:
- added Maxmind Geo data / analyzed Endpoints
- attempted to recreate images from packet data
- setup SSLKEYLOGFILE so I could decrypt encrypted packets in Wireshark
- explored env “environment settings”
- http1 vs http2 rabbit hole
- implicit packet analysis
- tried to set up tshark and pyshark cmdline tools
- unknown protocols lookup
Analysis Synopsis
After quieting down my local network, killing apps, disabling utils, stopping explicit requests I was still left with surprising amount of packets. Of the almost 9000 packets tracked for a little over 25 minutes, grant it probably too long, that reduced down to 42 unique destinations.
Of those 42 they even reduced further to 14 uniques by my own categorizations of “WHAT IS IT?”
| WHAT IS IT? | Notes |
| adobe | various adobe |
| amazon | aws |
| apple | lots of apple |
| cointick | crypto tracker |
| crashplan | work backup |
| elif’s phone | device / phone |
| Eurupe Central Bank? | Biggest What? Still not sure why this is happening? |
| github CDN? | unsure why w/ all apps closed? |
| google - user data maybe gmail? | googleuserdata - internet says used to be google+ |
| google home, pixel, or chromebook? | too many google devices (-‸ლ) |
| google wifi | router |
| microsoft | MS Office |
| my ipad | device / phone |
| my iphone | device / phone |
Most of which seemed to be devices on my local network talking back and forth but there were a few things that stood out. More on that below.
Exploration in Depth
For basic syntax and UI tools I also found this cheat sheet helpful.
Geo data and Endpoint Analysis
In class we looked at analyzing Endpoints and to get the most out of that we needed to link some geoIP data to Wireshark. The how to from the Wireshark cheat sheet was pretty straight forward and setup was smooth.
I found most of my Endpoints unsurprisingly were in the US. The large majority appeared to be hosting / CDN which makes sense.
HOSTING / CDN Amazon, Akamai, Google, Natcoweb, CLOUDFLARENET, EdgeCast, Akamai, Fastly, HighWindS3
The remaining Endpoints were mostly related to ads, lots of ad data going on.
ADS - AdSafe, Criteo, Outbrain, AppNEX, Adform, BidTellect, DoubleVerify, MediaMath, Rubiconproject, FreeWheel, Smartadserver
Followed by some analytics.
ANALYTICS - Omnitue, Quatcast
Image recreation from packet data
I asked about this in class and wanted to try it for myself. I navigated to insecure site and found a packet containing image data. I followed the HTTP stream, copy and pasted what I received from the source (website) into a text doc and saved it as a jpg. Unfortunately I couldn’t open any of the various ways I tried to do this. I did find the ‘File /EXPORT OBJECTS / HTTP’ tool which does allow you to get to the images from a pcap file but it wasn’t really what I wanted to do.
Setup SSLKEYLOGFILE and Explicit Packet Analysis
The cheatsheet also mentioned a way to set up SSLKEYLOGFILE to save private keys exchanged in the browser and then use that I Wireshark to decrypt and further analyze encrypted packets. OH! That sounds fun!
After a little trial and error I got it going. The cheatsheet is a little outdated with the newer versions of Wireshark. It says add the SSLKEYLOGFILE to the SSL protocol but now its just listed as TLS etc.
I found a better explanation of setting up the the SSLKEYLOGFILE here.
Which lead me to looking into printenv and general environment settings.
export SSLKEYLOGFILE="/Users/<account_name>/sslkeyfile"
'export' is for temporary env settings
printenv shows all environment settingsEven though the “export” cmd was “temporary” I used unset SSLKEYLOGFILE to remove the environment entry.
Using the ssl key log did show a little more data, but still when I followed the packets everything still appeared encrypted. It did however show me a little more detail on what the unencrypted packets were, where encrypted just showed TLSv1.2 protocols etc.
Packets encrypted
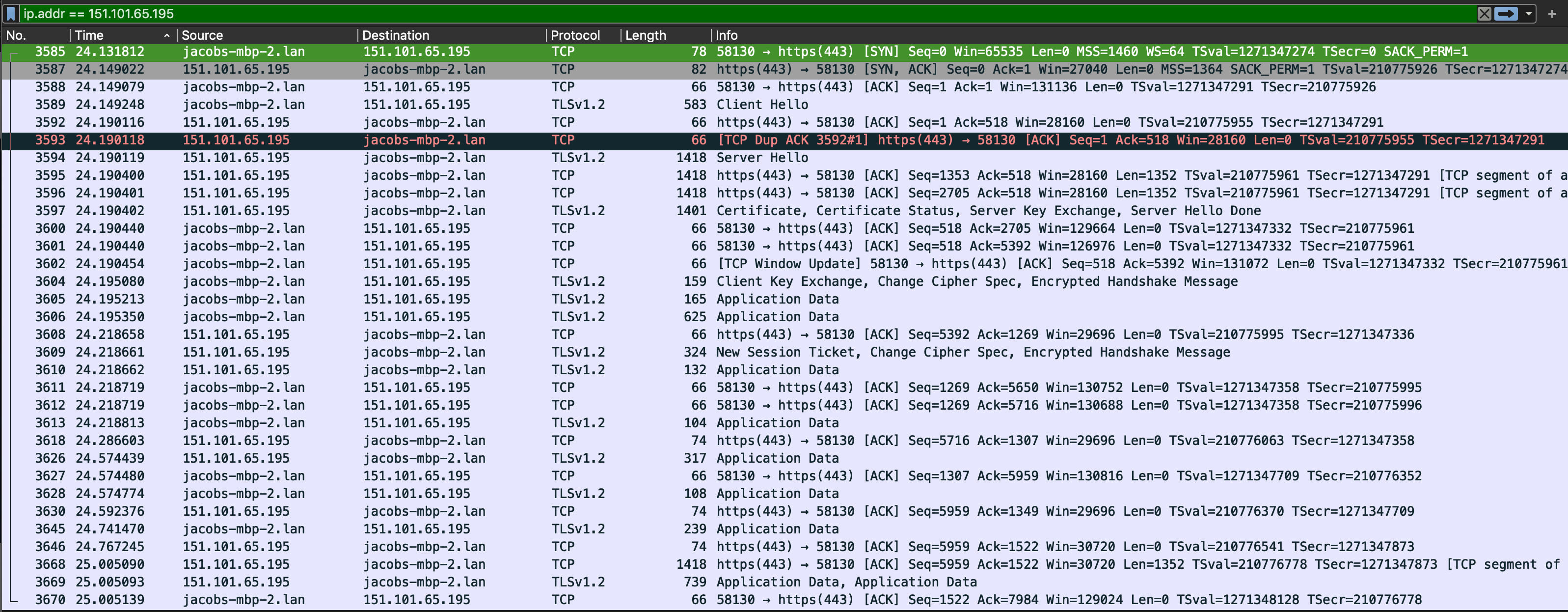 encrypted packets
encrypted packets
vs
Packets decrypted
 decrypted packets
decrypted packets
Looking at the decrypted packets, I can now see they are mostly HTTP2 protocol and various HEADERS, SETTINGS, WINDOW_UPDATES, GET requests and RST_STREAM etc.
This led me down 2 rabbit holes.
1) What is HTTP1 vs HTTP2 - who knew there was a new version introduced in 2015.
2) What is the “MAGIC” frame? (circled in red above) Anything “magic” deserved some investigation. Reading the above article helped me better understand some of the benefits of multiplexing and sending things in binary with HTTP2 and from what I gathered, the “MAGIC” frame is a handshake between the client and server regarding the use of HTTP2 and what settings to use. Further info here.
I also looked into RST_STREAM to find it was a “remote stream termination” msg saying my browser already had the file the server was trying to push.
Implicit Packet Analysis
As mentioned above I turned everything off, and let Wireshark do its thing. There was still a lot of information being exchanged.
I sifted through the pcap file and developed a lengthy filter !() rule.
((((((((((((((((((((((((((ip.src != 54.147.234.117) && !(ip.src == 192.168.86.217)) && !(ip.src == 35.175.85.133))<br>
&& !(ip.src == 192.168.86.22)) && !(ip.src == 192.168.86.250)) && !(ip.src == 54.209.113.211))) && !(ip.src == 40.115.22.134))<br>
&& !(ip.src == 192.168.86.21)) && !(ip.src == 162.222.40.109)) && !(ip.src == 162.222.40.109)) && !(ip.src == 17.248.187.69))<br>
&& !(ip.src == 17.248.187.69)) && !(ip.src == 192.168.86.29) &&!(ip.src_host ~ .crashplan.)) && !(ip.src == 104.17.138.178)) <br>
&& !(ip.src == 35.241.23.245)) && !(ip.src == 35.241.23.245)) && !(ip.src == 104.17.139.178)) && !(ip.src == 104.17.139.178))<br>
&& !(ip.src == 17.248.135.120) && !(ip.src_host ~ .adobe.)) && !(ip.src == 151.101.0.133)) && !(ip.src == 0.0.0.0)) <br>
&& !(ip.src == 0.0.0.0)) && !(ip.src == 104.17.141.178)) && !(ip.src == 17.253.15.204)) && !(ip.src == 17.253.15.204))<br>
&& !(ip.src == 17.248.187.15)The biggest take away being the wildcard filter which wasn’t mentioned on any of the cheat sheets I found. Luckily StackOverflow to the rescue.
Example: remove all domains containing ‘adobe’
!(ip.src_host ~ .adobe.)With my filters in place, I again took my remaining packets and pasted into Excel and ran a duplicate filter. This again reduced down to a pretty small number all of which I could Identity…
| No. | Time | Source | Dest | WHAT IS IT? | Protocol | Length | Info |
| 11 | 0.780403 | 104.40.147.142 | my lpatop | microsoft | TLSv1.2 | 106 | Application Data |
| 2 | 0.019728 | 17.57.144.6 | my lpatop | apple | TCP | 66 | hpvirtgrp(5223) → 53818 [ACK] Seq=1 Ack=70 Win=1452 Len=0 TSval=2737240856 TSecr=1283349021 |
| 9 | 0.757312 | 192.168.86.1 | my lpatop | router | DNS | 125 | Standard query response 0x3647 PTR 250.86.168.192.in-addr.arpa PTR jacobs-mbp-2.lan |
| 2004 | 515.665734 | ec2-52-20-152-99.compute-1.amazonaws.com | my lpatop | amazon | TLSv1.2 | 97 | Encrypted Alert |
| 2010 | 515.724412 | polka.typekit.com | my lpatop | adobe fonts | TCP | 82 | https(443) → 64540 [SYN, ACK] Seq=0 Ack=1 Win=26847 Len=0 MSS=1460 SACK_PERM=1 TSval=393678755 TSecr=1283864242 WS=256 |
| 2266 | 579.928224 | www-ecb-europa-eu.ax4z.com | my lpatop | CoinTick? European Central Bank? | TCP | 74 | https(443) → 64547 [SYN, ACK] Seq=0 Ack=1 Win=43440 Len=0 MSS=1460 SACK_PERM=1 TSval=2655725640 TSecr=1283928283 WS=4096 |
Except for one… European Central Bank???!?! What the heck?
Why am I receiving packets from www-ecb-europa-eu.ax4z.com? I do run a crypto track menu app so I thought that might be it, but closing that down still resulted in ecb.europa.eu Packets.
Searching various sources google, reddit, etc were no help. I could not source a definitive reason for these packets.
I did find some conflicting reports about whether it was malicious or not.
Malicious = false src
Malicious = true src
Both from the same site so who knows ¯_(ツ)_/¯
Looking further at my implicit packets there were ALOT of apple packets. Same process to get uniques, reduced 500 down to 5. Mostly DNS related.
| No. | Time | Source | Dest | WHAT IS IT? | Protocol | Length | Info |
| 40 | 9.886725 | gateway.fe.apple-dns.net | laptop | Apple DNS | TLSv1.2 | 105 | Application Data |
| 4570 | 933.212867 | usnyc.ce.apple-dns.net | laptop | Apple DNS | TCP | 82 | https(443) → 64580 [SYN, ACK] Seq=0 Ack=1 Win=43440 Len=0 MSS=1460 SACK_PERM=1 TSval=346698163 TSecr=1284281221 WS=32 |
| 5050 | 934.715547 | edge-063.usnyc.ce.apple-dns.net | laptop | Apple DNS | TCP | 82 | https(443) → 64585 [SYN, ACK] Seq=0 Ack=1 Win=43440 Len=0 MSS=1460 SACK_PERM=1 TSval=940758542 TSecr=1284282671 WS=32 |
| 5306 | 950.176515 | caldav.fe.apple-dns.net | laptop | Apple DNS | TCP | 82 | https(443) → 64589 [SYN, ACK] Seq=0 Ack=1 Win=43440 Len=0 MSS=1460 SACK_PERM=1 TSval=649710292 TSecr=1284298066 WS=32 |
| 5555 | 1029.577615 | keyvalueservice-g.fe.apple-dns.net | laptop | Apple DNS | TCP | 82 | https(443) → 64596 [SYN, ACK] Seq=0 Ack=1 Win=43440 Len=0 MSS=1460 SACK_PERM=1 TSval=2279378554 TSecr=1284377378 WS=32 |
Set up tshark and pyshark cmdline tools
I attempted to set up some cmd line tools but didn’t have much success.
I first installed tshark. Hoping to be able to get “unique” packet results. Surprisingly there wasn’t a way to filter that in the GUI and the internet said to do it with the cmd line tool.
Pyshark python implementation / wrapper of tshark
I could get tshark to work but didn’t have enough time to work through the cmds to get more meaningful data than just using the GUI. Wanting to get uniques led me to the Excel dedupe process mentioned above.
Pyshark kept erring out and I think I was missing some dependencies maybe.
Unknown Protocol Lookups
ARP The Address Resolution Protocol is a communication protocol used for discovering the link layer address, such as a MAC address, associated with a given internet layer address, typically an IPv4 address. This mapping is a critical function in the Internet protocol suite. ARP works between network layers 2 and 3 of the Open Systems Interconnection model (OSI model). The MAC address exists on layer 2 of the OSI model, the data link layer, while the IP address exists on layer 3, the network layer.src
HSRP (Hot Standby Redundancy Protocol)is first hop redundancy protocol which provide Network Engineers flexibility to provide gateway level redundancy in case of primary fails. In HSRP we can have two or multiple routers to be part of one group. one router will be active out of them and second would become standby, rest all the routers would be in listen state. so in case of active router fail, Standby router be promoted to active. src
PKTGEN Pktgen is a tool for high-speed packet generation and testing. It runs in the Linux kernel, and is designed to accommodate a wide range of network performance tests.Pktgen is a tool for high-speed packet generation and testing. It runs in the Linux kernel, and is designed to accommodate a wide range of network performance tests.src
OCSP OCSP stands for Online Certificate Status Protocol and is used by Certificate Authorities to check the revocation status of an X.509 digital certificate.src
DNS vs MDNS - Like DNS, mDNS also resolves domain names to IP addresses. mDNS operate at local network level unlike conventional DNS which operates at global level. It works in conjunction with DNS-SD (service discovery) protocol in zeroconf network. Zero configuration network does not require manual operation. src
Final Thoughts
The internet is still mysterious and as mentioned Wireshark is a beast of an application. It was fun to slowly chip away at my packet traffic and dive deeper into my relationship with machines and the internet.
It would be nice to run this process on other devices and compare.